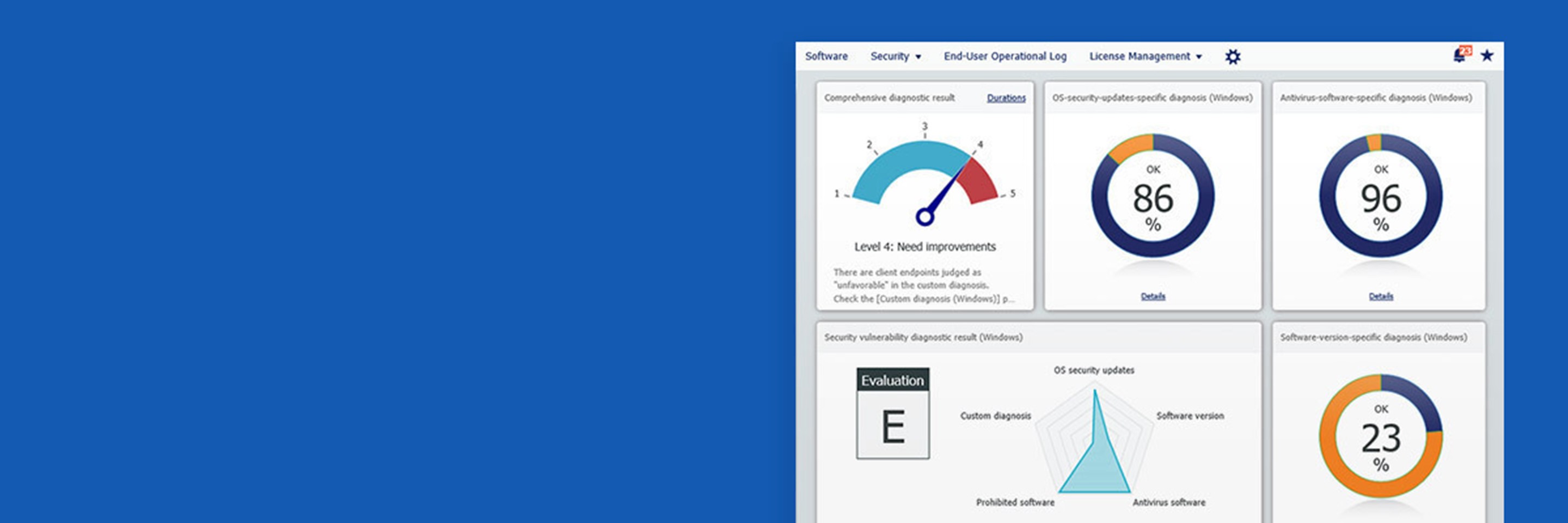
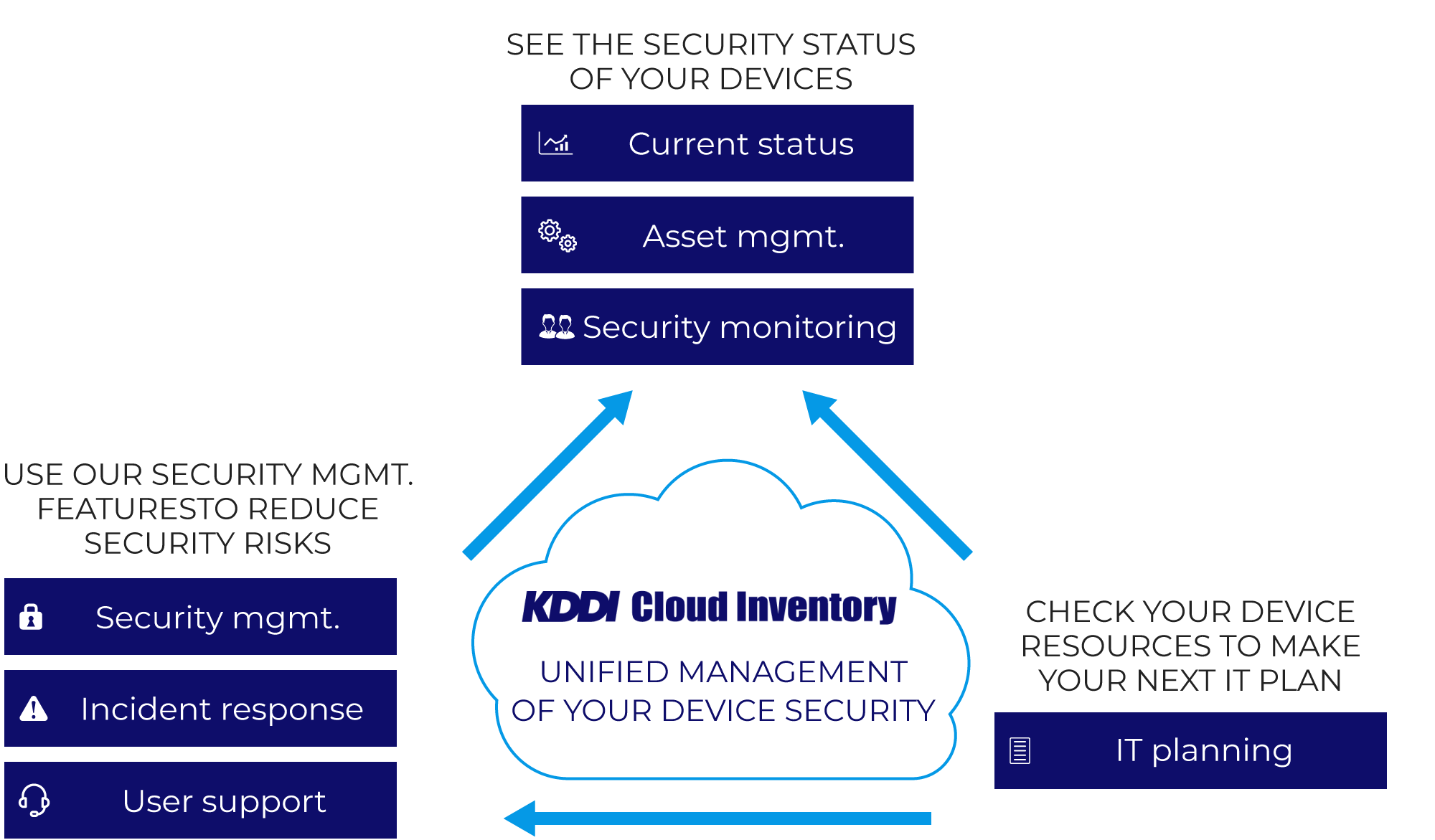
What is KDDI Cloud Inventory?
Unifies your device security process

Usable from anywhere
Manage from anywhere in the world where you have an Internet connection

Multi-device support
Manage multiple device types, including Windows devices, Mac devices, and mobile devices

Automated security management
Automatic detection and display of devices with security vulnerabilities

3 languages supported
A Web console available in Chinese, English and Japanese

Global contracts
Purchase with a single Japan contract, or purchase through local contracts in other countries’ currencies

Wide variety of security controls
External device restrictions, hard disk encryption, behavioral detection and other security features
An optimal solution for those troubled by these issues

How can I manage the security of
PCs taken off company grounds?

How can I check for devices
that violate company policy?

How can I stop privately-owned
smartphones from connecting
to the company network?
Features
FunctionalityA wide variety of security-related functions
In addition to security management, KDDI Cloud Inventory provides HDD encryption, external device (USB memory, etc.) restrictions, PC operational log acquisition, behavioral detection (malware detection), and more.
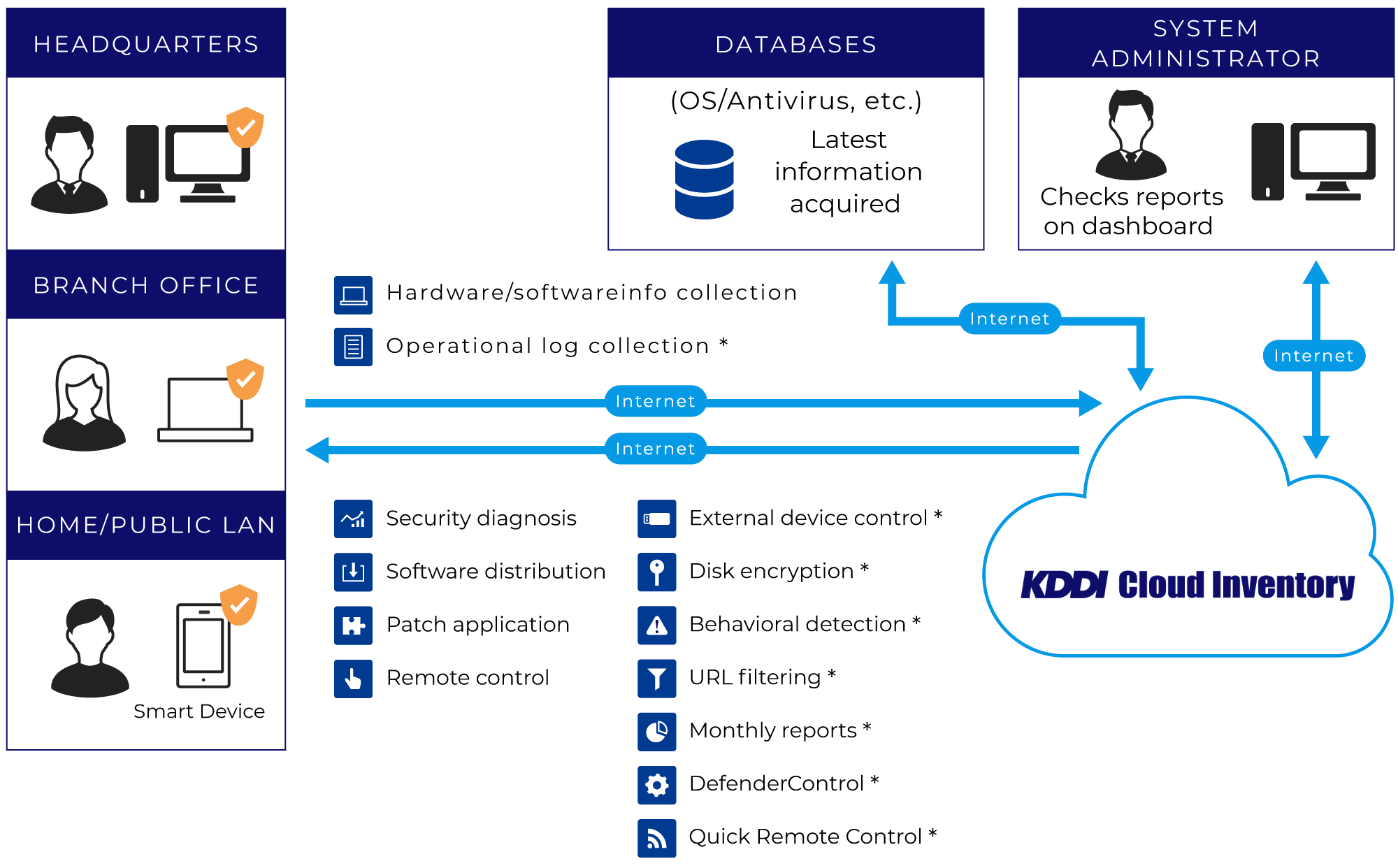
- * indicates for-pay option
EfficiencyMake large reductions in your workload
Automation of security management (automatic vulnerability diagnoses) and asset management frees up your busy system administrators and makes usage easy.
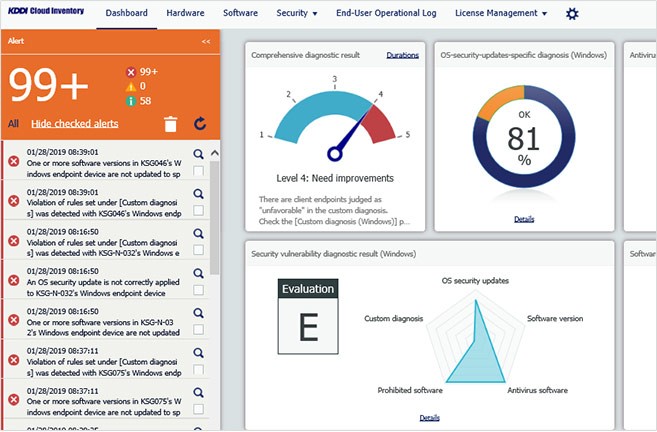
Automatic vulnerability diagnoses
Provides a list of PCs lacking the latest OS and software* updates. By automatically located at-risk PCs, your management workload is greatly reduced.
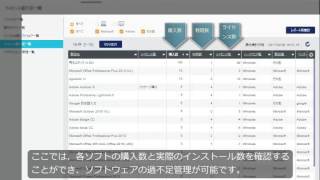
Asset management
Once a day, information is collected from your managed devices, allowing you to manage your assets with accurate information, without the work of collecting it yourself.
- * Image is for reference only.
- * Software such as Java, Flash, Adobe Reader/Flash Player, Internet browsers, etc.
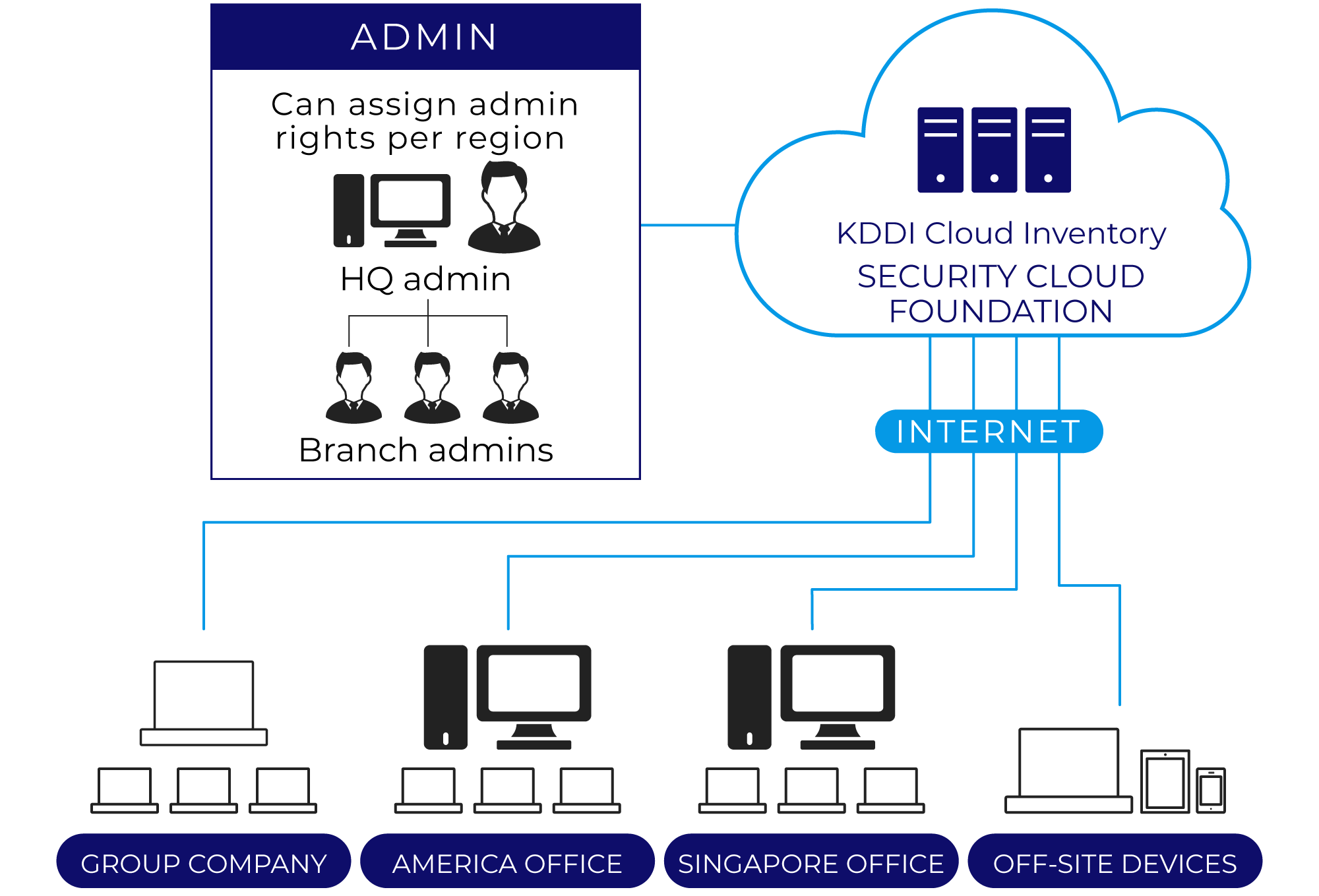
FlexibilityCloud-based system means you can start small
All you need is an Internet connection. Easily scale as needed, from managing a few dozen devices to tens of thousands.
Functions
Asset management
| Hardware and software lists | Covers the range of data needed for IT asset management. CSV output is possible. |
|---|---|
| License management reports | Reports on the license usage status of Microsoft Office, Adobe products, and other software. |
| Standalone PC management | Collect inventory information for stand-alone PCs. Realize management of all PCs within your company. |
| Application portal | Lists the applications that can be installed for each company and department. |
| Lease/rental management | Takes regular inventory of lease/rental IT assets and equipment and gives warning about the lease/rental periods, etc. |
| Asset search | Search assets by criteria such as asset management number, manufacturer, department, serial number, user, software, etc. |
| Filter criteria | When distributing applications or policies, identify the target client device easily by using filters. |
| Granting user/ administrator permissions |
Give group administrators authority for policy settings, remote control, client management, and external media management to manage clients for each group. |
| Alert emails | Security summary alert emails are automatically sent to registered email addresses once a day. |
| Survey collection | Survey users and collect their responses as inventory data. |
| Printer management | Collect information such as printer type, IP address and manufacturer name. Change printer driver settings remotely. |
Security Management
| Rooting/Jailbreak detection | Detect client devices that have been rooted or jailbroken, with notification emails sent to administrators. |
|---|---|
| Forced software updates |
You can apply policy so that client devices are always automatically updated to the latest versions of software such as Windows and Adobe Reader. |
| Application startup restrictions | Restrict the applications that can be started on client devices. You can also forcibly close suspicious applications running on client devices. |
| Network connection control | Remotely distribute and apply Wi-Fi settings and VPN settings to client devices using profiles. Restrict client devices to permitted access points only. |
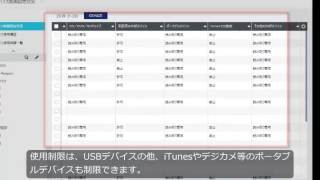
| SD card and Bluetooth restrictions |
Prevent information leakage by restricting the use of SD cards and Bluetooth. |
| Prevention of ISM client suspension | If the client service is stopped, the service is automatically restarted. |
| Configuration profile deletion detection | Detection of when the policy configuration profile of a client device has been deleted. |
| Emergency application restrictions | Prohibit use of particular applications on a client device in case of emergencies, such as when the device goes missing, etc. |
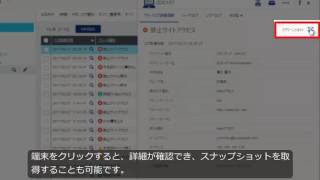
| Acquisition of locational information | If a device is lost, you can find it by obtaining location information from it and displaying it on Google Maps and Bing Maps. |
| Remote lock Reset to factory defaults |
When theft or loss occurs or a device has been in long-term policy violation, you can remotely lock the device or reset it to factory defaults. |
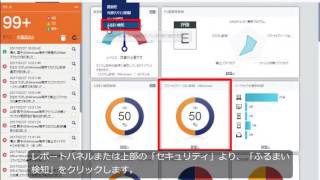
| Automatic security diagnosis | Your organization’s security level is rated on a five-point scale based on the recommended security settings and the current status of the managed client devices. |
| Policy setting for when there is a violation | You can set a policy for use in the event of a client device violating security policy, and switch offending devices over to that policy as needed. |
| Antivirus software application status report |
Displays whether anti-virus software is installed or not, pattern file version, etc. |
| Personal data acquisition consent function | Use this function to ask client device users for consent in obtaining data such as inventory and operation logs that could include personal information from their devices. |
| Operation console operation logs | Record and view operation logs for the management console. |
| new Defender Control* |
Allows you to control Windows Defender settings and see the existing settings and malware detected for each managed device. |
| User operation logs* | Acquire client device operation status via the Internet, and discover fraudulent activity. Collect logs covering the most recent three months. |
| new Log analytics* |
Collect PC operation logs that show who did what and when. Check operational status, or take advantage of various features including Webconference recording. Long-term storage (up to 7 years' worth of logs) lets you quickly investigate even past incidents. |
| HDD encryption* | Prevent information leakage due to device theft, loss, etc., by encrypting the entire hard disk and using pre-OS startup authentication. |
| External media use restrictions* | Restrict MTP/PTP communication with USB memory, smartphones, digital cameras, etc., to prevent unnecessary usage. |
| Behavioral malware detection* | An engine that anticipates malware attack patterns detects, defends, and removes unknown threats. |
| Communication device restrictions* | 1. Restrict communication with Bluetooth devices 2. Restrict communication by specifying IP addresses 3. Restrict access point connectivity with SSID specifications |
| URL filtering* | Being a cloud-based system means there is no initial investment required for internal servers, and secure Web access is available anytime, anywhere, and on any device. (Only for Japanese language sites) |
- * indicates for-pay option
Remote Management
| Software distribution File distribution |
Distribute and remotely install software and files. |
|---|---|
| Distribute registry values | Add/edit registry values, delete entries, and delete keys on client devices via the Internet. |
| Application deployment and uninstallation |
Distribute applications to client devices. ISM client version upgrade is also possible by distributing client modules. |
| Remote control (simplified version) |
Allows operation of (remote control) and file transfer to client devices via the Internet. |
| new Quick Remote Control (high-performance version)* |
Enables administrators to perform high-speed, stress-free remote control of PCs at regional offices or of those working from home. |
- * indicates for-pay option
Other Features
| Monthly reports | Provision of inventory information at the beginning of each month as a report file (Excel format) |
|---|
- * The functions and prices you can provide differ depending on the node you are using. Please contact us for details.
Videos
Brochure
Contracts outside Japan
Comprehensive customer support
KDDI local staff will provide support in the local language not only for the Japanese side but also for local staff on the overseas side before and after the solution is introduced.
You can also entrust us with the support of your contract.
In addition to Japanese contracts, we also accept contracts on the overseas side. We are able to respond to your budget and business structure.
If you are considering using it overseas, please contact us from the following.
(Provision details and charges, etc., differ depending on the providing country. Please contact us.)
Inquiries about the Service
KDDI Corporate Sales Representative will consult with you and provide you with an estimate for the introduction.
If you have any questions, please feel free to contact us.