- Behaviour Detection / AI / Machine Learning
- Detect and block known and unknown threats
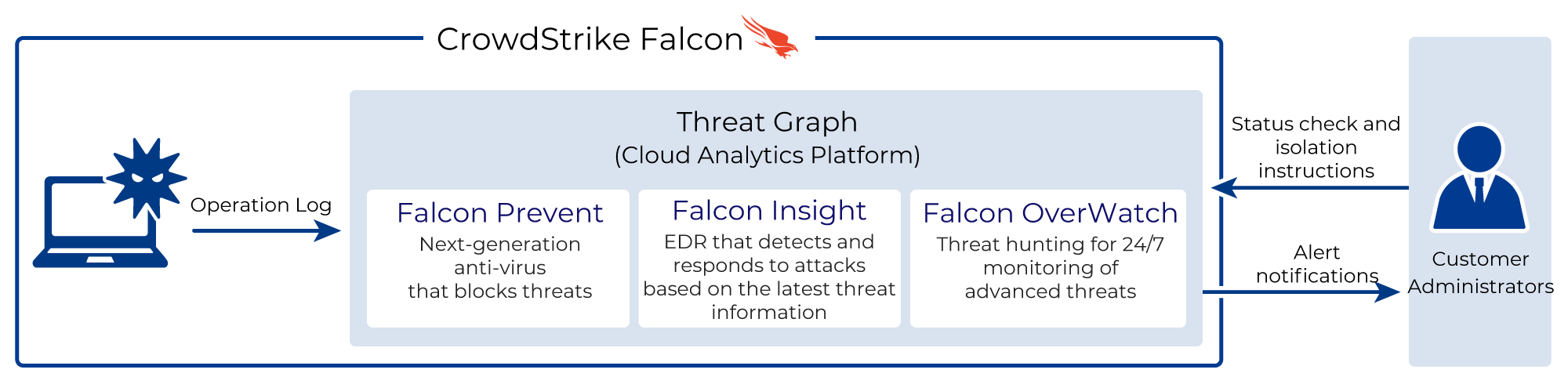
CrowdStrike Falcon
CrowdStrike Falcon is an endpoint security solution that stores and monitors log data collected from endpoints connected to an organization’s network to detect and prevent suspicious behavior and cyber attacks.
Next Generation Antivirus, EDR (Note 1)Protect your devices and information assets from external threats, with a focus on threat hunting capabilities.
- Note 1) EDR: abbreviation for endpoint detection and response. Monitors the operation and behavior of endpoint devices and takes action in the event of an incident.
Background of EDR Solution Needed
As remote work and cloud services are increasingly being used, cyber attacks targeting endpoints are becoming more sophisticated. Security solutions such as traditional anti-virus products and firewalls have become harder to prevent attacks and increase threat risk.
Therefore, it is necessary to build an IT environment based on zero trust architecture that is not bounded by the boundaries of internal network or Internet.
EDR solutions not only protect against cyber attacks at the entrance, but also proactively contain risk by detecting and responding quickly to malware in the event of an attacker infiltrating an organization.
The EDR solution enables incident detection and immediate response, followed by rapid investigation and analysis.
- Note 2) EPP: abbreviation for Endpoint Protection Platform. Protect devices from malware infections such as computer viruses.
CrowdStrike Falcon
CrowdStrike Falcon is Falcon Prevent (Next Generation Antivirus) , Falcon Insight (EDR), Falcon OverWatch (Threat Hunting by Security Experts) , it on a single platform. Effectively detect and prevent breaches as a countermeasure against emerging attacks such as ransomware that is created every day.
List of functions by plan
The Falcon Prevent
- Detect known and unknown threats by leveraging the vast amount of data gathered from endpoints
- Protect against malware with signature-free AI / machine learning engines
- Behavior detection technology protects against fileless attacks
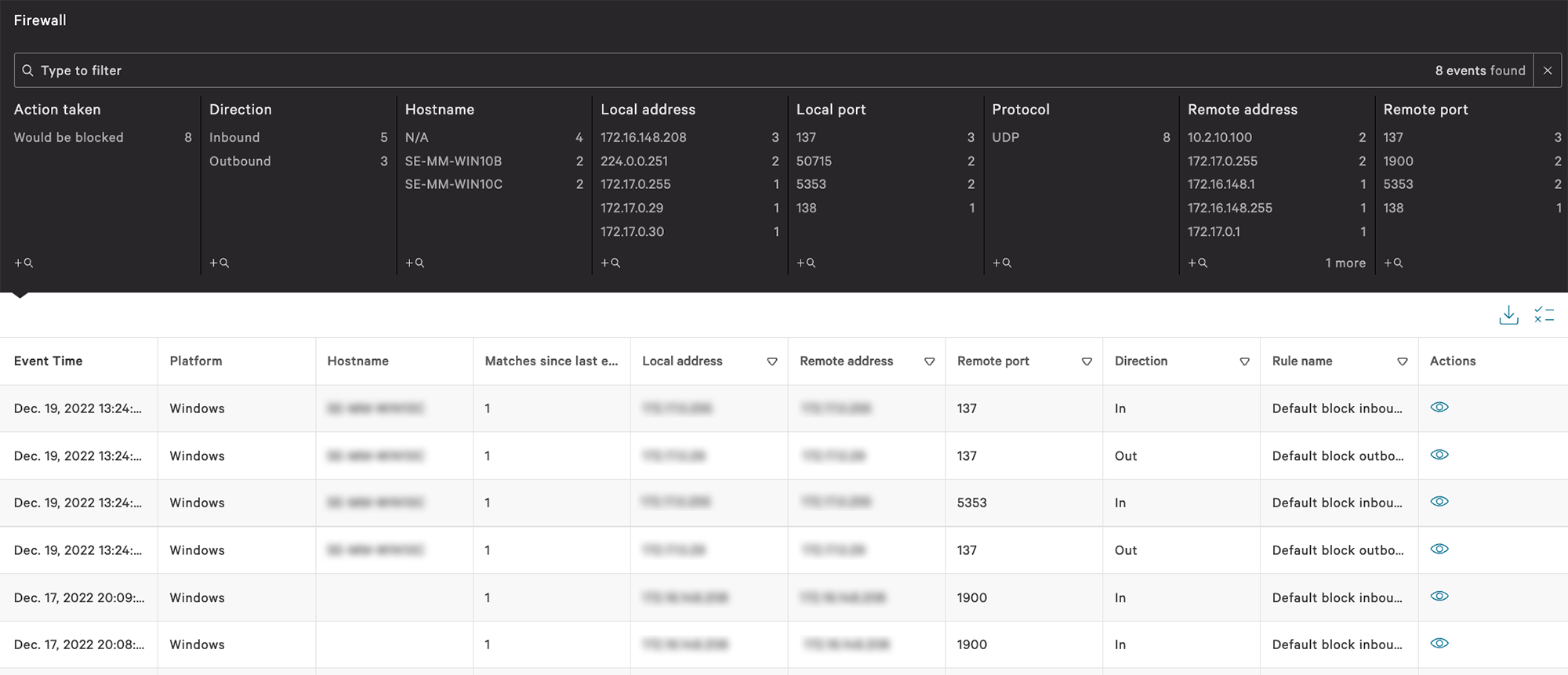
Features / Specifications
| Block attacks that cannot be protected by AV Block |
The latest AI and machine learning engines prevent fileless attacks, exploits and more. In addition to IOC (Indicator of Compromise), IOA (Indicator of Attack) can be used, and behavioral blocks can be used by AV. |
|---|---|
| High deffence | The av-comparatives Real-World Protection Test (August-November) showed high performance with a block rate of 99.9%. (Note) |
| Lightweight agent | No need for tasks that significantly degrade performance, such as signature updates or disk scans. A lightweight agent of about 25 MB with less than 1% CPU utilization. It’s a lightness that users don’t realize the agent is in. |
The Falcon Insight
- Detects a wide range of known and unknown threats, from malware to fileless attacks
- Remotely isolate and repair hosts from the management console
- Investigate alerts by alert and multiple alerts by incident
- Visualize pre- and post-detection processes in chronological order
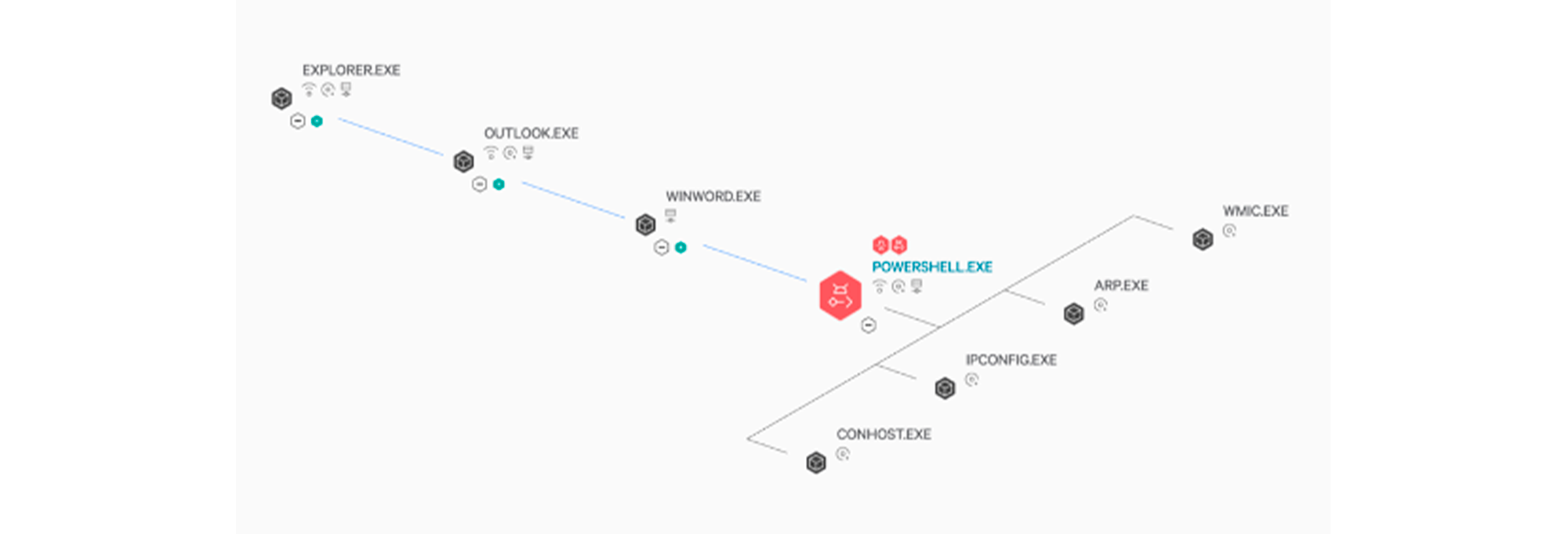
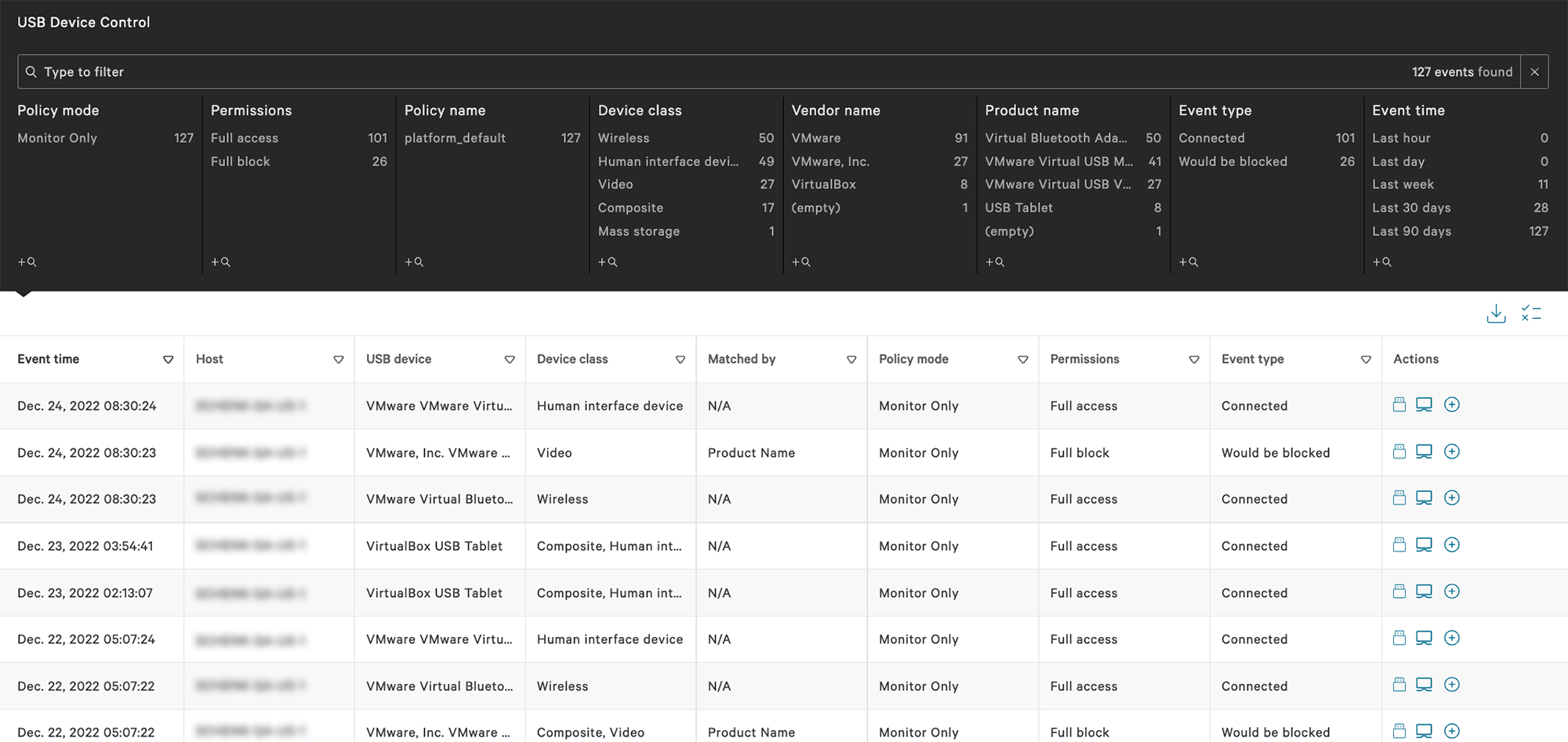
The Management screen displays a series of attacks as a process tree, along with threat ranking.
Intuitive visibility into the full picture of front-and-back attacks, plus drill-down for more detail, enables rapid investigation and response.
- The picture is an image.
Features / Specifications
| Agent operating in kernel mode | Agents operating in user mode will be stopped by the attacker. Agents operating in kernel mode are very difficult for attackers to stop working. |
|---|---|
| Variety of available logs | Since EDR detects from logs, the more log types, the more accurate the detection of threats. Capture and detect more than 200 types of logs, including process registry file network Windows event logs. |
| Enhanced response capabilities | Another pillar along with the detection of the EDR is the handling function. It provides the ability to isolate from the network and perform a variety of remote operations on endpoints. It works in kernel mode, so you can get information such as READ / WRITE files, writes to the registry, and memory dumps. |
| Visualized Process Tree | Improve analysis efficiency by graphically displaying the attack process in a tree. |
Additional Menu
Falcon overwatch
- Threat hunting service from CrowdStrike security experts
- 24/7/365, expert manual monitors attacks by logs uploaded to the cloud which hard to detect by next-generation antivirus and EDR
- Notify and assist administrators in responding to high-urgency attacks
Features / Specifications
| Security Expert | Experts from around the world use tools to isolate events that are uploaded from around the world and thoroughly suspicious to discover attacks that are difficult to detect only with tools that cannot be found with AI or machine learning. For those that are clearly under attack, notify the administrator directly by email. The experience and know-how accumulated by dealing with the latest attacks every day is reflected in the detection logic on the product side. |
|---|---|
| 24/7/365 constant monitoring | Unlike general threat hunting, which consultants enter and investigate for a period of time, we constantly monitor your environment 24/7/365, so you can stop the attack at any time. |
Post-implementation operational support
Operating an EDR solution requires accurate event awareness when an alert is detected and prompt action after detection. Without an organization such as SOC, operational loads are often a challenge because of the need for tuning and expert knowledge to properly manage large volumes of alerts.
KDDI Managed Security Services help you monitor and operate the security of your IT environment with 24/7/365 real-time log analysis and detection, as well as analyst research and analysis.
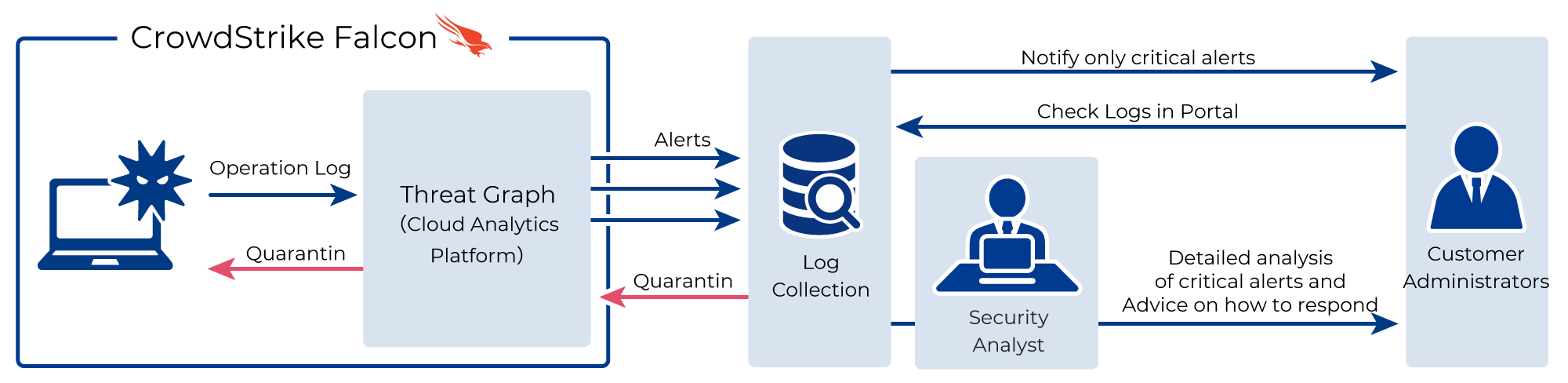
You can view incident information and log data through a centralized customer portal that manages multiple security service log incidents, extract important events from a vast range of logs, and provide advice on cause identification and response policies.
With a comprehensive log analytics platform, security talent, and operational skills and know-how, customers can deploy EDR Solution Zero Trust Security without having to prepare new security monitoring systems or human resources.
For more information, Check KDDI Managed Security Services.
Contracts outside Japan
Comprehensive customer support
KDDI local staff will provide support in the local language not only for the Japanese side but also for local staff on the overseas side before and after the solution is introduced.
You can also entrust us with the support of your contract.
In addition to Japanese contracts, we also accept contracts on the overseas side. We are able to respond to your budget and business structure.
If you are considering using it overseas, please contact us from the following.
(Provision details and charges, etc., differ depending on the providing country. Please contact us.)
Asia/Oceania
America
Europe/Middle East/Africa
Inquiries about the Service
KDDI Corporate Sales Representative will consult with you and provide you with an estimate for the introduction.
If you have any questions, please feel free to contact us.